WordPress is far and away the most widely-used content management system on the web, but that popularity comes at a price. It’s also the most attacked CMS. Not because it’s un-secure, but because attackers know that a WordPress vulnerability is a gateway to tens of millions of websites.
As soon as a WordPress website goes online, automated bots begin to probe it for weaknesses. That’s why it’s critically important to security harden WordPress sites, ensuring that they have the smallest possible surface area for attackers to target.
Security hardening was once a long and complicated manual process, but WP Toolkit for cPanel makes it a one-click affair. This article will explore some of the ways WordPress vulnerabilities are exploited and how WP Toolkit protects sites against many common attacks.
Common WordPress Vulnerabilities
Every vulnerability is unique, but most attacks against WordPress sites fall into one of four categories:
- Brute force and dictionary attacks: Attackers attempt to guess security credentials such as usernames and passwords. Attacks of this type are carried out by bots that can quickly flood WordPress authentication systems with a deluge of login attempts.
- Denial of Service (DOS) and Distributed Denial of Service (DDoS) attacks: Bad actors bombard sites and networks with requests and data, consuming resources, degrading performance, and potentially taking them offline. WordPress includes a system called XML-RPC, which is often used in denial of service attacks.
- Core, plugin, and theme vulnerabilities: Bugs in code can be exploited to circumvent authentication systems, upload malicious code, or gain extra privileges. Bad actors often look in a site’s files for clues about the sort of attack it is vulnerable to.
- Code injection attacks: Running malicious code is a goal of many bad actors. They scour WordPress sites searching for vulnerabilities that will let them inject PHP, JavaScript, or SQL code.
WP Toolkit for cPanel implements features and security measures that protect sites against each of these attack types.
Security Hardening with WP Toolkit for cPanel
cPanel’s WP Toolkit is a complete WordPress management solution with an intuitive interface. You can think of it as a single dashboard for controlling all of your WordPress sites. It automates WordPress hosting tasks, including installation, updates, and backups. It also surfaces configuration tweaks that you’d otherwise have to dig around in the admin interface or edit configuration files to change.
WordPress security hardening is one of the places where WP Toolkit really shines. First, it applies fixes for critical vulnerabilities during installation, so sites are secure before they go online. Second, it scans existing sites for suboptimal security settings and can fix them at the click of a button.
We’ll have a look at some of the security fixes it applies in a moment, but first, we’ll show you just how easy it is to security harden a WordPress site with cPanel.
To use one-click hardening, you will need:
- A cPanel instance with WP Toolkit installed
- A WP Toolkit Deluxe license.
You can find the WP Toolkit in Applications on cPanel’s main page. Sites are listed on the overview page with status information and configuration switches.
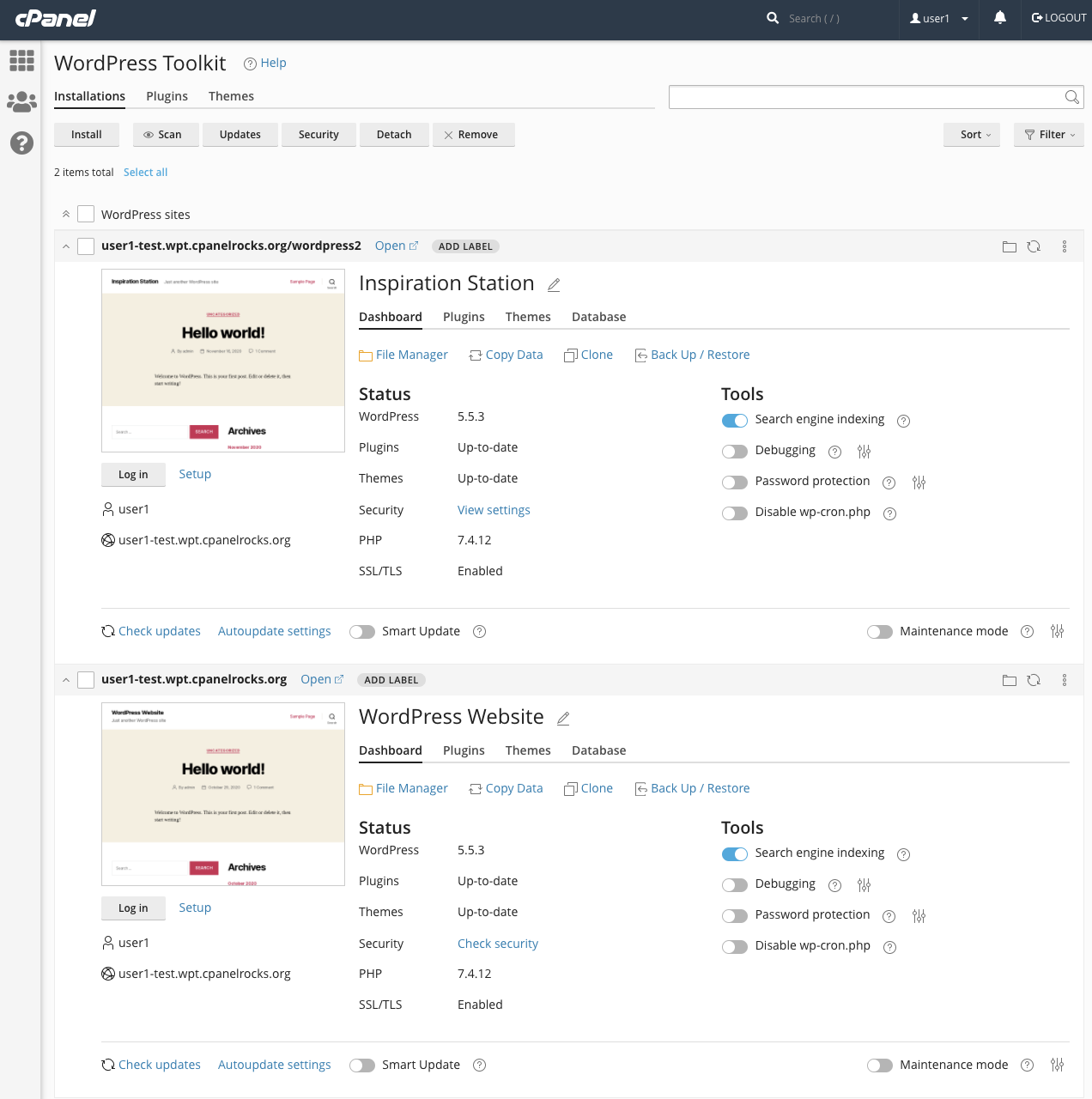
If you take a closer look at the second site, you will notice that, under the Status heading, the Security line reads Check Security. WP Toolkit scanned the site and noticed that several non-critical security measures have not been applied. The first site has already been hardened, so it displays View Settings.
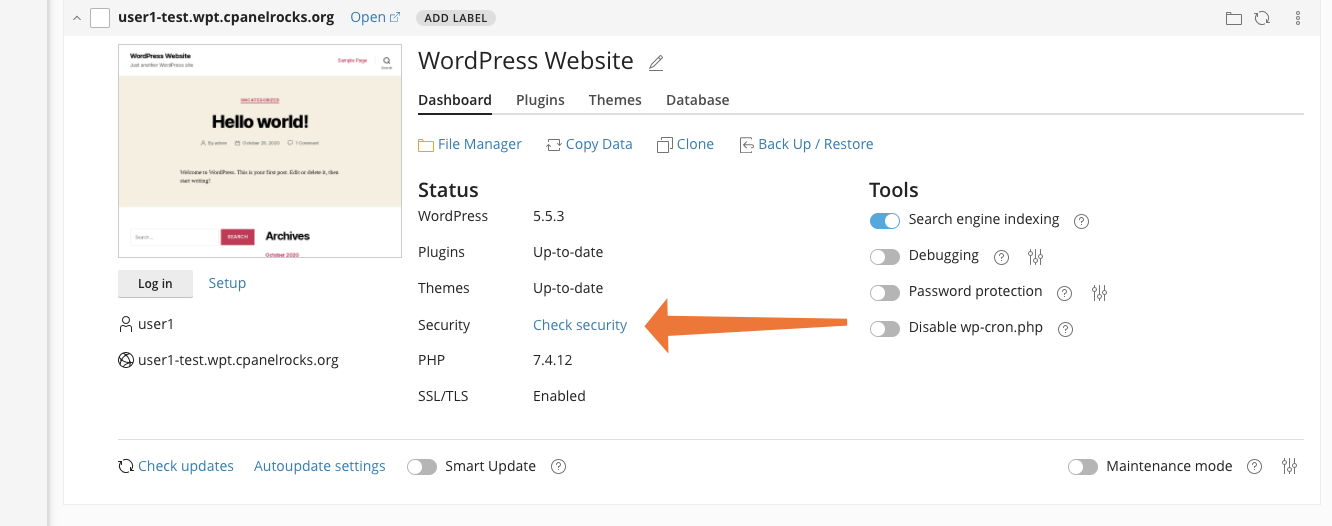
You might also see Fix Security here, which means that critical security measures have not been applied.
We can click on the status message to open the Security Status panel, which displays all of the security measures the WP Toolkit can apply.
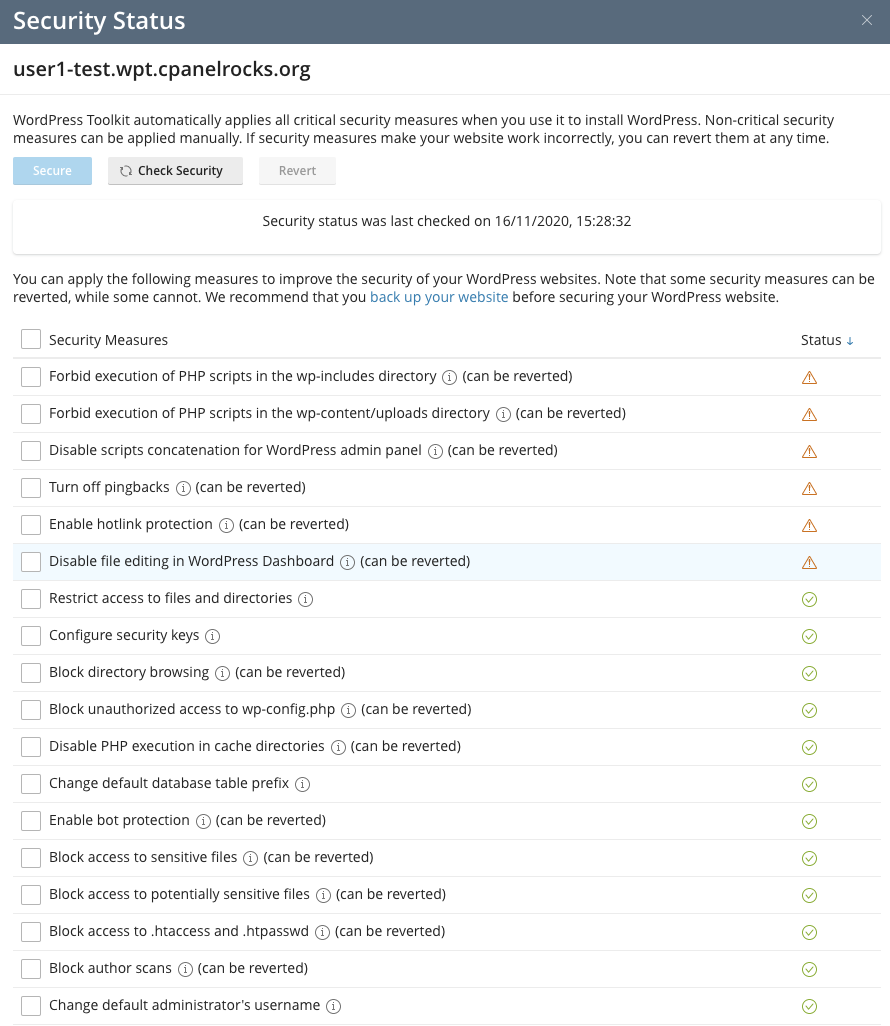
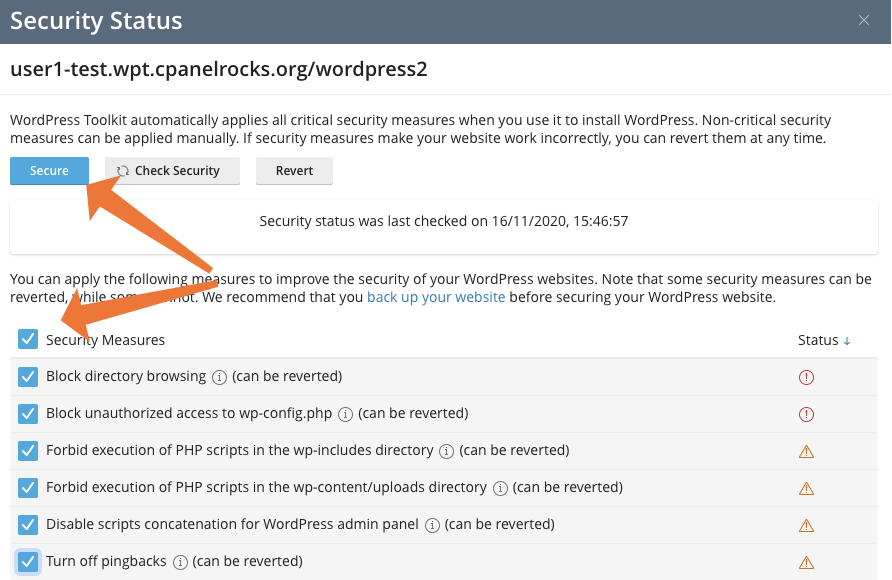
You can apply each measure individually by checking the adjacent box and clicking Secure. They can be reverted, where possible, by selecting them and clicking Revert. But we want to secure our WordPress site in a single click, and to do that, we’ll select the Security Measures checkbox at the top of the column and then click the Secure button.
One-Click Hardening for Multiple WordPress Sites
What if you host dozens of WordPress sites? It would be time-consuming to secure each one individually, so you’ll be happy to hear that you can use the WP Toolkit to secure any number of sites at the same time. On the overview page, click the Security Tab.
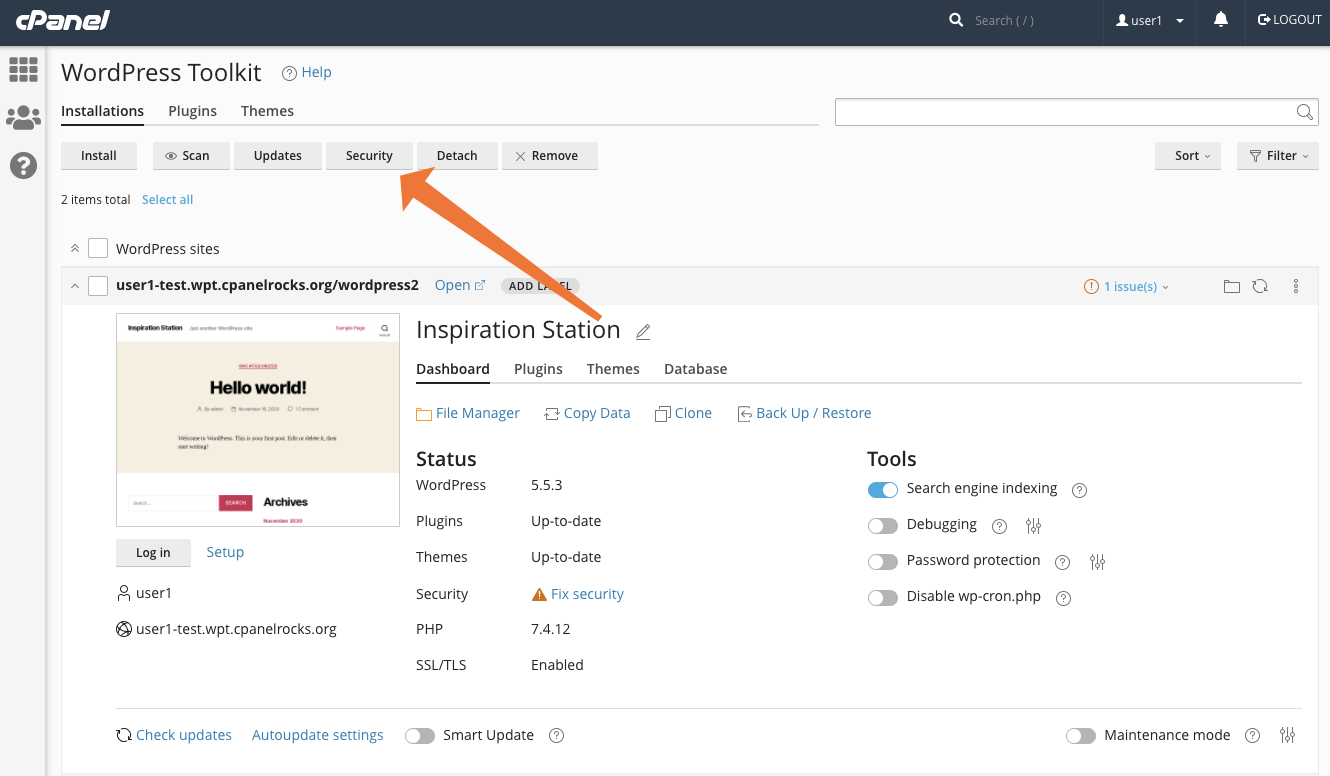
cPanel displays a list of sites and their security status. Use the checkbox next to each site to select those that aren’t fully hardened, and then click the Secure button at the top of the page.
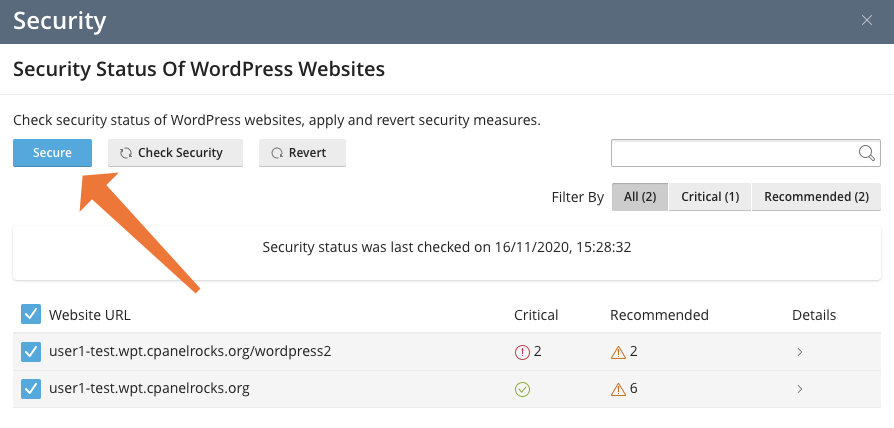
You’re given a chance to specify which security measures to apply, and then cPanel automatically hardens all selected sites. You can use this method to secure dozens or even hundreds of WordPress sites simultaneously.
Security Settings in WP Toolkit
WP Toolkit applies almost 20 security measures, but we’d like to highlight a handful of the most important here.
- Forbid execution of PHP files: The toolkit forbids the execution of PHP files in the wp-includes and wp-content/uploads directory. Both are common targets of bad actors and malicious users who upload PHP code and attempt to execute it.
- Block directory browsing: The files inside WordPress’s directories contain information about plugins, themes, and other code that might reveal vulnerabilities. The Toolkit makes it impossible for any non-authenticated user to look in directories. It also sets secure file permissions for the wp-config file and all other files and directories.
- Enable bot protection: Allowing bots to scan your site is a security risk, as well as a waste of server resources. The WP Toolkit blocks bad bots to limit a site’s exposure.
- Change default administrator’s username: When first installed, WordPress creates a user with administrative privileges called admin. Bots and other bad actors often target admin with brute force and dictionary attacks.
- Turn off Pingbacks: When a WordPress website links to your site, it sends a ping, which results in a comment on your blog that records the link. Pingbacks rely on the insecure XML-RPC protocol, which can be abused to overwhelm a site’s resource in a denial of service attack.
- Enable hotlink protection: Hotlinking allows external sites to embed or display images hosted on your server. You gain little benefit from hotlinking, and it can become a significant drain on server and network resources.
Finally, the WP Toolkit makes it simple to quickly update WordPress Core, plugins, and themes in a unified interface, as well as to manage automatic updates. Plugin and theme vulnerabilities are the most common WordPress exploit, and regular updates are the only way to protect sites from vulnerabilities in their code.
Restoring Backups with WP Toolkit
To finish, let’s look at one more security essential that cPanel simplifies: restoring backups. A recent backup is a lifeline if all else fails. It allows users to restore a compromised site to a secure and uninfected condition, and, with the WP Toolkit, making and restoring backups takes seconds.
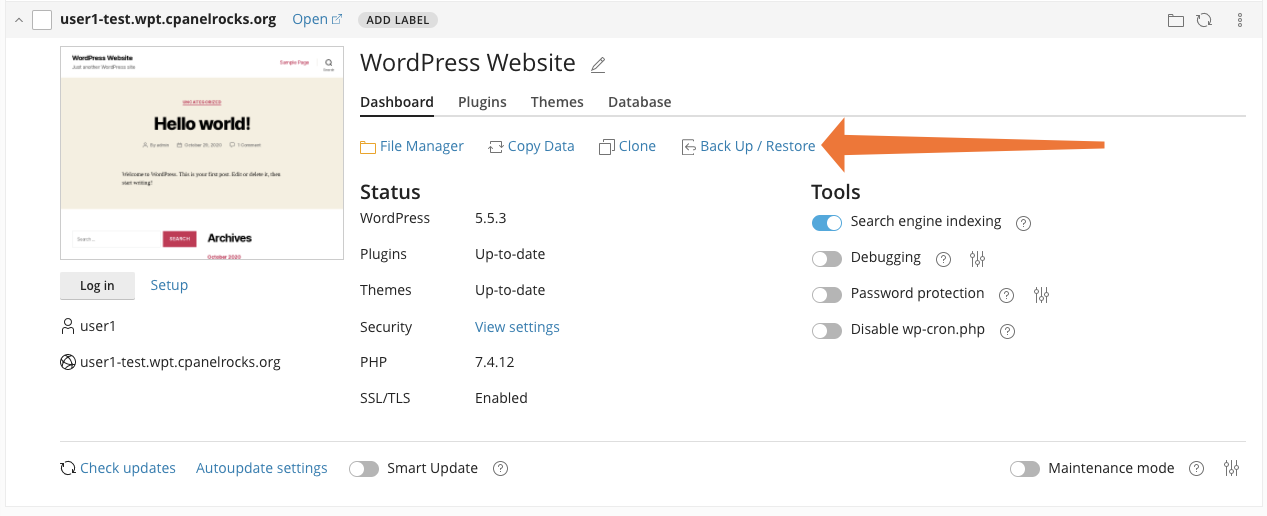
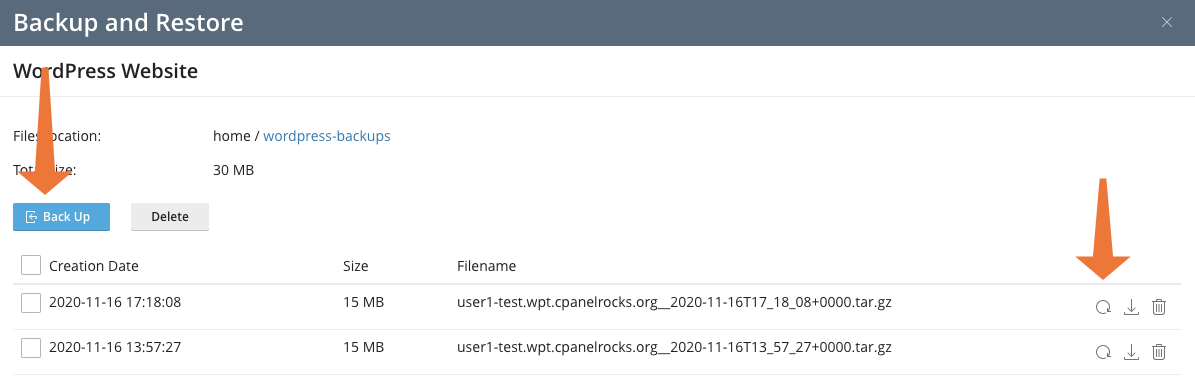
To create a backup, click the Back Up button. If you have previous backups, they are listed on the page. To restore your WordPress site and its database to an earlier state, choose a backup file and click the restore icon, as shown in the next image.
Secure WordPress Hosting with cPanel
The WP Toolkit makes it easier than ever to build a secure WordPress hosting platform with cPanel. Security hardening is now a one-click process, allowing hosts to protect servers, sites, and users without a long and expensive manual hardening process.
As always, if you have any feedback or comments, please let us know. We are here to help in the best ways we can. You’ll find us on Discord, the cPanel forums, and Reddit.


